If your company uses an LDAP server (Active Directory, 389 Directory Server, etc.), you can use the user data from an LDAP catalogue in ELMA.
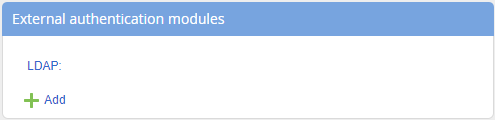
Fig. 1. External authentication modules unit
This unit saves all the configured authentication modules. By default, the list contains an empty LDAP module, available only for editing. To edit a module, use the

button; to delete a module, use the

button (these buttons are displayed when you mouse over a module).
To add a new authentication module, click

. The
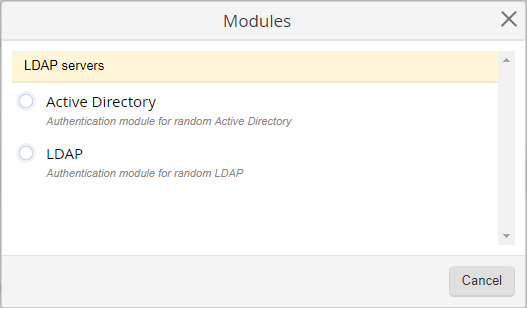
Modules dialog box will appear (fig. 2).
Fig. 2. Modules dialog box
Select an authentication module type (Active Directory, LDAP) and click Add.
Configuring LDAP connection
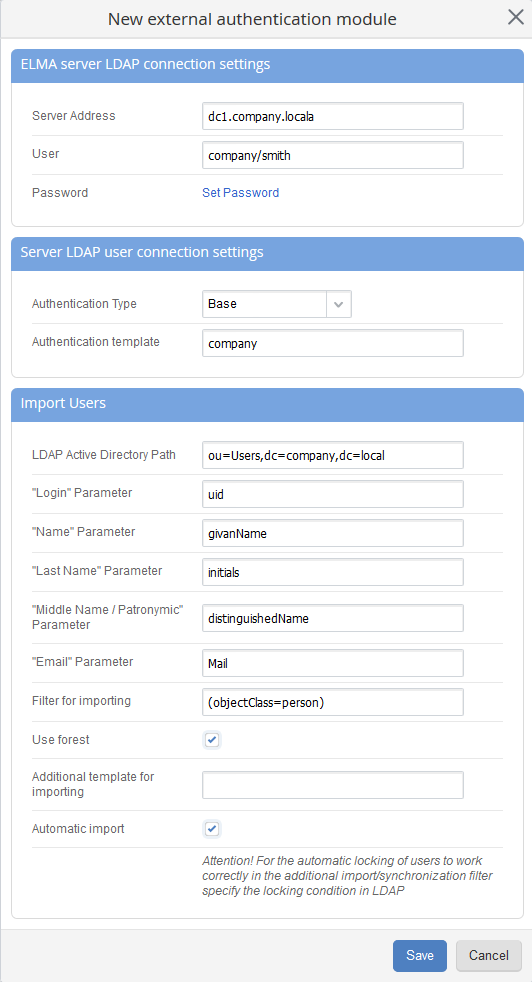
When you add a new LDAP module, a window will open (fig. 3). To successfully connect to LDAP, fill in the fields, as described below.
Fig. 3. LDAP settings
"ELMA server LDAP connection settings" unit
In the Server Address field, specify the IP address (filled in automatically) or the domain name, used to address the server. If the server is installed on a port, different from the default LDAP port (389), you also need to specify it separated by a column (e.g. "dc1.company.local:8389", where the server name is dc1.company.local and the port is 8389).
In the User field, specify the name of the user, used for logging in to the LDAP server.
In the Password field, specify the password of the account, by clicking Set up Password.
"Server LDAP user connection settings" unit
In the Authentication type field, select one of the four types:
-
Base (during data transfer, the login and password are encrypted using base64);
-
Secure (during data transfer, not the login and password are transferred, but the hash, calculated on their basis);
-
With encryption (authentication data are protected with the Kerberos protocol);
-
|
Attention!
When you integrate with the LDAPS server, choose the base authentication type and import certificates to the server into Trusted roots.
|
In the Authentication template field, specify the domain name, used for addressing the server. If necessary, you can add the user login, e.g. company\{$login}.
"Import Users" unit
LDAP Active Directory Path - to specify a path to users use the ADSI connection string syntax ("short" form or format of name attributes).
Attributes:
-
OU – Organization Unit – organization unit or department that contains such objects as users, contacts, groups and others.
CN – Common Name – relative name. User, contact, group or another object that usually does not have child objects.
DC – Domain Component – domain name component.
For example, to get the users of the Users root group of the company.local domain, you need to use the following path "cn=Users, dc=Company, dc=local"
Next, define the correspondence between ELMA and LDAP fields:
-
"Login" Parameter – specify the field, used on your LDAP server for storing the user login;
-
"Name" Parameter – specify the field, used on your LDAP server for storing the user name.
-
"Last Name" Parameter – specify the field, used on your LDAP server for storing the user's last name.
-
"Middle Name / Patronymic" Parameter – specify the field, used on your LDAP server for storing the user middle name.
-
"Email" Parameter – specify the field, used on your LDAP server for storing the user email.
Filter for importing – filter, used in queries to LDAP server when importing users.
If you check the Use forest box, one or several linked trees that use the catalogue information will be connected.
If you check the Automatic import box, the users imported from LDAP will be synchronized according to the condition, specified in the Filter for importing field. Automatic import is performed every 10 minutes. If an LDAP user was not found during synchronization, it will be locked in the system. If an imported user is locked in the system but found in LDAP, it will not be unlocked.
The system also provides Manual import, which searches for locked and/or unlocked users during the import. If an LDAP user was not found during import, it will be locked in the system. If an imported user is locked in the system but found in LDAP, it will not be unlocked.
Configuring connection to Active Directory
LDAP integration settings vary for different LDAP servers. This section illustrated LDAP settings for Microsoft Active Directory. Connection configuration for other LDAP servers is described in their respective documentation.
To add a new Active Directory authentication model, select Active Directory when creating a module (fig. 2). A settings window will open (fig. 3).
This example describes integration settings with an LDAP server of the contoso.com domain. As the user account, on behalf of which the import is performed, "LDAP Auth" is used. All the necessary user accounts are stored in the "Users" catalogue of the LDAP server. LDAP server's IP address is "192.168.0.126" and it uses the default port:
Server Address – 192.168.0.126
User – cn=LDAP Auth, cn=Users, dc=contoso, dc=com
Authorization type – Base
Authentication template – contoso\{$login}
LDAP Active Directory Path – cn=Users,dc=contoso,dc=com
"Login" Parameter – SAMAccountName
"Name" Parameter – givenName
"Last Name" Parameter – SN
"Email" Parameter – Mail
Filter for importing – (&(objectCategory=person)(objectClass=user))
Copyright © 2006–2019 ELMA