Configuring single sign on for a web farm
Before reading this article, read the guides on configuring a web farm and single sign-on.
In this example, we will be using:
- Active Directory domain named mycompany (mycompany.com);
- ARR controller computer name – elma;
- Names of computers with ELMA – elma1 and elma2;
- name of the user who will run ELMA – mycompany\elma_user.
Preliminaries:
- In the Active Directory domain, create a user on whose behalf ELMA server application pools and the application pool on the ARR controller will be started. Or use an existing user of this domain. In this example – mycompany\elma_user.
- Make sure that the ARR controller computer and the ELMA server computers are in the same domain as the user (in this example – mycompany).
To configure single sign-on:
1. Configure a web farm following the instructions (https://kb.elma-bpm.com/article-1745.html) and make sure that it works.
2. Configure single sign-on following the instructions (https://kb.elma-bpm.com/help/EN/Platform/content/Admin_Through_autorization_index.html). The following settings must be changes in these instructions, to ensure single sign-on on a web farm:
- In the dialog box for selecting Windows authentication provider (step 4) and put Negotiate in the first place and click OK:
.png)
- click Advanced Settings in the right menu and in the opened dialog box check Enable Kernel-mode authentication and click OK:
.png)
- go to the Configuration Editor of the added SSPI application;
.png)
- in the drop-down list select system.webServer -> security -> authentication -> windowsAuthentication;
.png)
- set True for the following parameters authPersistNonNTLM, authPersistSingleRequest, enabled, useAppPoolCredentials anduseKernelMode;
.png)
3. In the advanced settings of application pools set the start on behalf of mycompany\elma_user:
- for the ELMA servers (elma1 and elma2) – for the ELMA site pool.
.png)
4. Enable anonymous authentication (disable all the other authentication types) in the Default Web Site on the controller side (elma server). Go to the Authentication section of this site and leave only the Anonymous Authentication enabled.
.png)
.png)
5. The next step is configuring the IIS application pool. In the advanced settings of application pools, specify mycompany\elma_user as the identity:
- for the controller (elma server) – for the DefaultAppPool;
.png)
6. Set SPN for each ELMA server and controller (bind their addresses to the user, under whose account application pools will be running). You can do it using the SETSPN command (in the command prompt), or the ADSI Edit console (adsiedit.msc).
Example of using the command prompt:
SETSPN -S HTTP/elma.mycompany.com mycompany\elma_user
SETSPN -S HTTP/elma1.mycompany.com mycompany\elma_user
SETSPN -S HTTP/elma2.mycompany.com mycompany\elma_user
Example of using the ADSI Edit console:
In the CN=Users tree, find the elma_user and in its context menu click Properties.
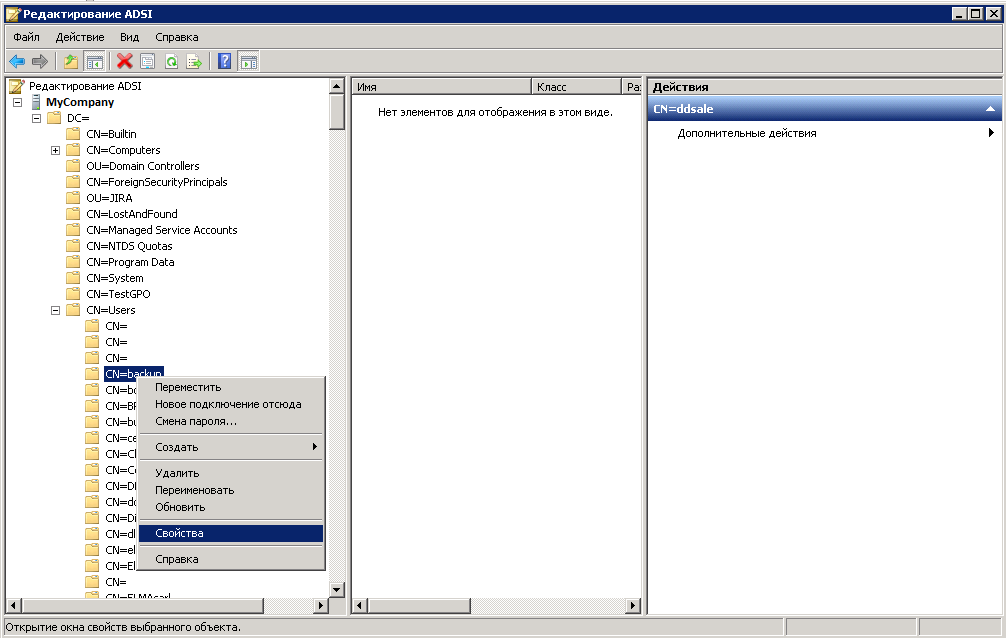
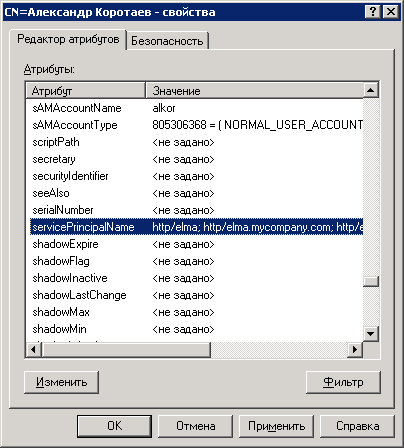
In the opened window, on the Attribute Editor tab, find the servicePrincipalName attribute, click Edit and add all the ELMA servers and the controller server.
7. Check that single sign-on works on each server and then on the controller server.
- at step 2 of this guide, place the Negotiate:Kerberos provider in the first place;
- at step 4 select Kerberos authentication on the controller side, i.e. leave only the Windows Authentication enabled and select Negotiate:Kerberos in the list of providers;
- follow the steps 5 and 6;
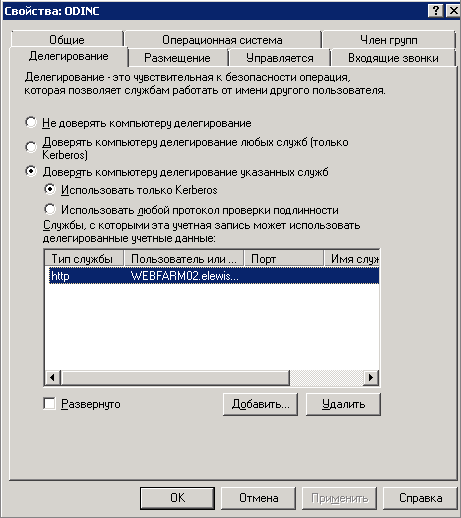
At the next step, configure delegating Kerberos to AD. For the controller, add the http service type and specify the farm server names; for the farm servers - add the http service type and specify the controller name:
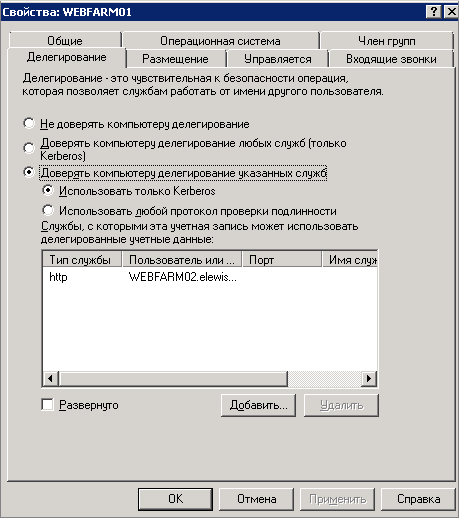
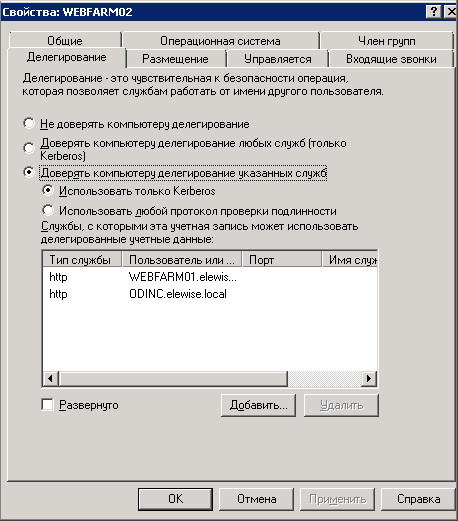
Therefore, you need to make sure that there are no duplicate names in the domain. For this, you can start cmd.exe and run the command setspn /x
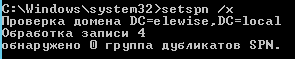
If duplicates are found, delete them.
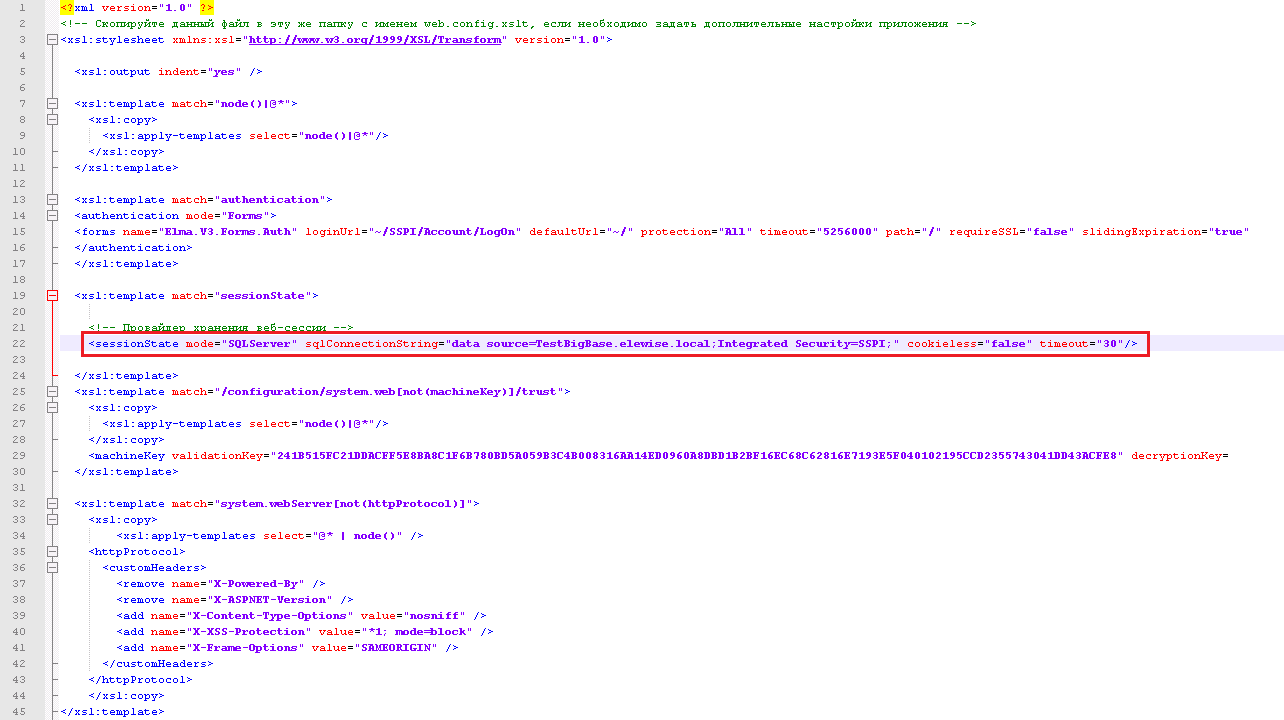
After that, configure the database connection file. Open the Configuration.config file and add the following line:
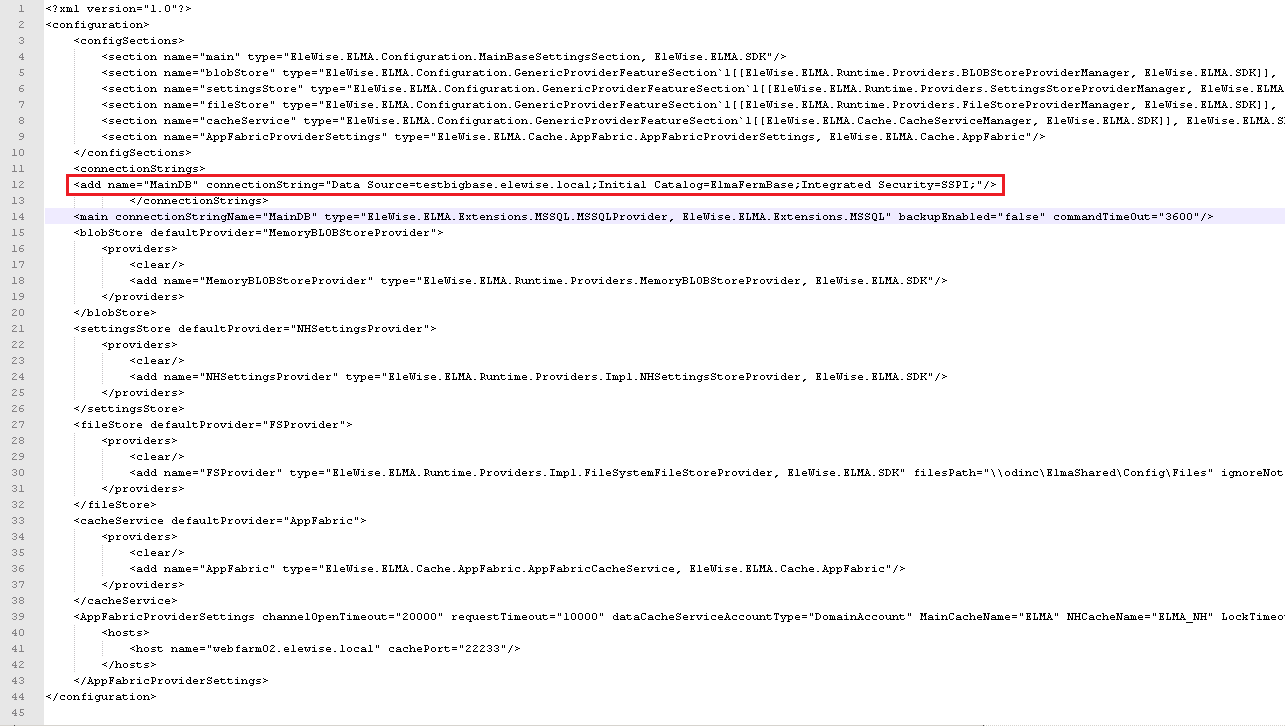
Also edit the file Web.config.xslt. Add the following line to this file:
For ELMA Agent to work with Kerberos, you need to start is the first time with the parameter USINGKERBEROSONWFBALANCE=True.
Kerberos is set up. Follow step 7.
In order for single sign-on to continue working correctly after updating of the web farm, it is necessary to do the following:
- create a copy of the Settings.config file in the …/<Folder with the ELMA system files>/Web/ folder;
- update the web farm;
- rename the updated Settings.config file in the …/<Folder with the ELMA system files>/Web/ folder in the following way: Settings_< version_number_of_the_updated_system >.config. For instance, Settings_3_13_13.config;
- move the previously copied file to the ../< Folder with the ELMA system files >/Web/
See also:
