To increase the security level, ELMA system provides a possibility to allow signing in only from trusted devices.
Trusted devices are:
To allow signing in to the system using only trusted devices, a user has to:
Signing in to the system as this user will be possible only from a device, added to the list. If you attempt to sign in from a device, not included in the list, the system will notify, that the user name or password is incorrect.
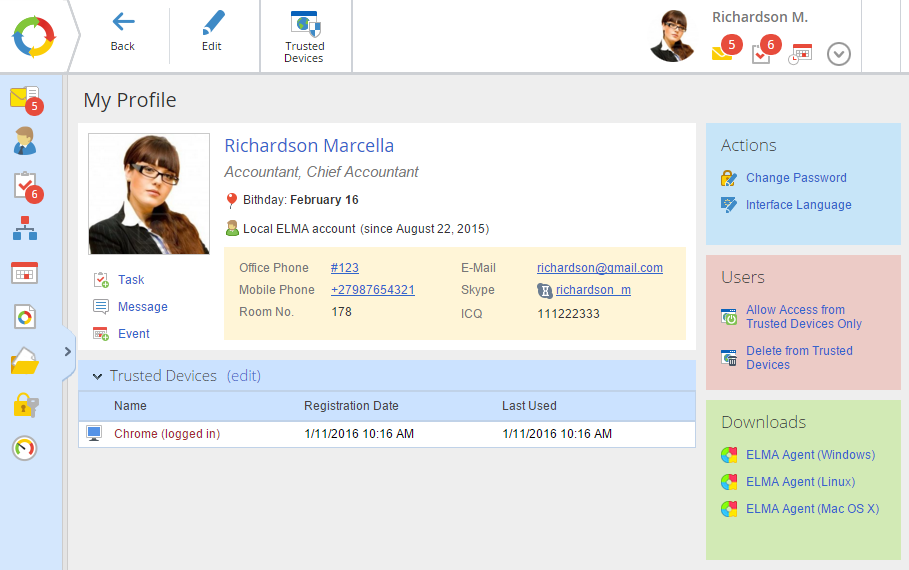
The list of trusted devices, created by a user, is displayed in their profile, Trusted devices section (fig. 3).
Add a trusted device
In order to add a browser or an Apple iPad to the list of trusted devices, sign in to ELMA from this device, go to your profile and click any of the three control items (fig. 1):
If you click edit the Trusted Devices section of the user profile will open (fig. 2).
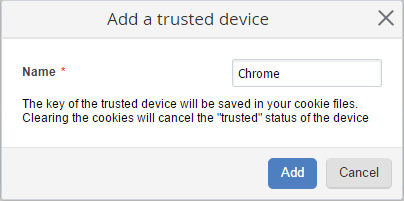
It displays the list of the user trusted devices. If you click Add to Trusted Devices, a window for adding a new trusted device will open (fig. 3). Enter the name of the trusted device in this window and click Add. The new trusted device will be displayed in the list of trusted devices (fig. 2).
|
|
|
Fig. 3. Adding a trusted device.
|
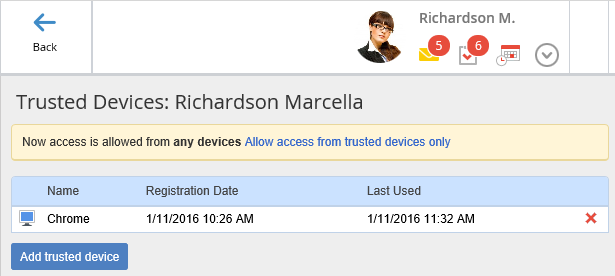
The list of trusted devices (fig. 4) can include an unlimited number of devices. Certificates are automatically added to the list of trusted devices, when bound to the user account.
|
|
|
Fig. 4. List of user trusted devices.
|
Enable sign in only from trusted devices
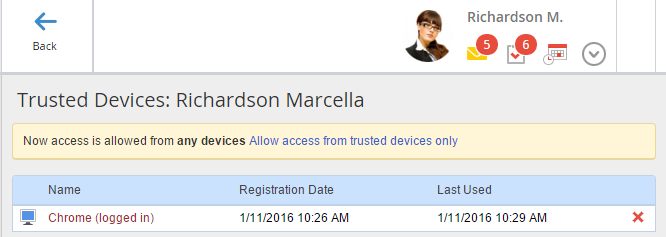
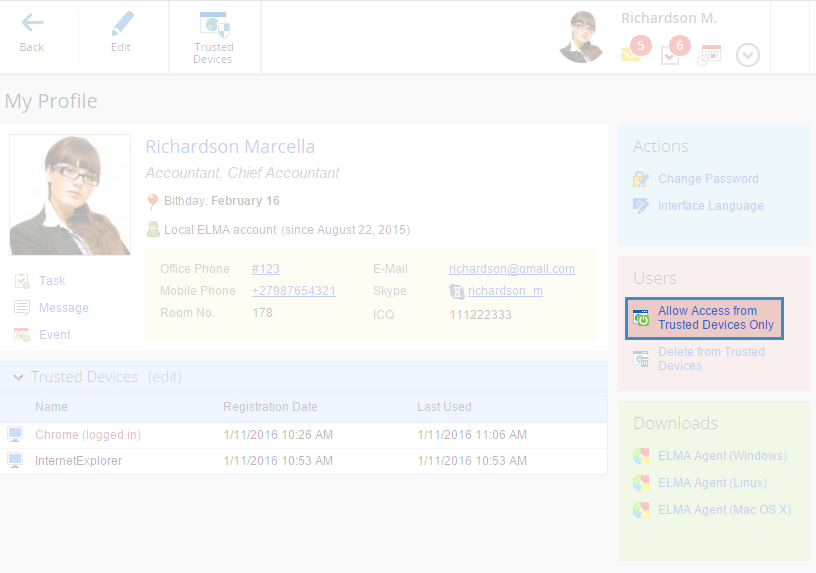
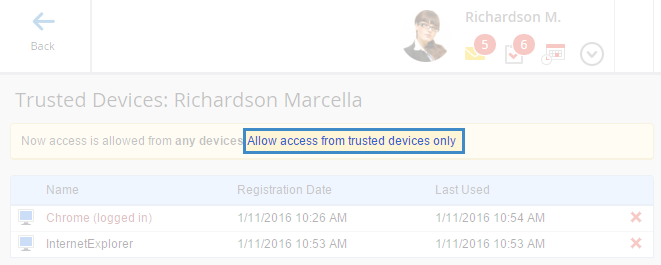
After you have created the list of trusted devices, you can allow signing in to the system only from trusted devices. To do so, click Allow Access from Trusted Devices Only (fig. 5, 6).
|
|
|
Fig. 5. List of user trusted devices.
|
A confirmation box (fig. 7) will open. Click Yes to enable signing in to the system only from trusted devices.
|
|
|
Fig. 7. The confirmation box.
|
Delete a trusted device
If signing in to the system only from trusted devices is enabled, after you delete a device from the list, it will be impossible to sign in from it.
To delete a trusted device from the list, go to the trusted devices editing page (fig. 4) and click the button, opposite the device, you need to delete from the list. When you click the button, a confirmation box (fig. 8) opens. Click Yes, to delete the device from the list.
|
|
|
Fig. 8. The confirmation box.
|
Manage trusted devices
To open the trusted devices management page, click Edit in the Trusted Devices unit (fig 1).
The trusted devices management page has the following functions (fig. 9):
-
-
-
Add trusted device – add a browser or an iPad, you signed in from, to the list of trusted devices. This button is available only if the browser or iPad, you signed in from, has not been added to the trusted devices.
-
-
It will be possible to sign in with login and password only from the devices in the list;
-
|
|
|
Fig. 9. Trusted devices management section.
|
The device, you are currently signed in to the system from, is colored brown and has "logged in" (fig. 4).
Copyright © 2006–2019 ELMA